Innovative role management - more than just RBAC
Smart but secure – with SecuRole® you finally have your role management under control.
Role management redefined: SecuRole® is an innovative concept to overcome the limits of the role-based access control approach (RBAC) and meet the needs of today’s security requirements, also in connection with cloud technologies.
The limits of RBAC
Role management exists to make sure that permissions are assigned correctly in an IT system. This involves using different concepts such as, for example, RBAC or ABAC (Attribute Based Access Control). Since access and approval processes in companies call for automated workflow today, it is necessary to assign permission to individual persons or groups and put them into the system. Especially for role management according to the RBAC principle, a complex, confusing, assignment framework often arises over time, which leads to complex restructuring projects. In that approach, roles are mostly represented by user groups. A role is assigned to a user by membership in a respective group, whereas access rights are assigned to groups.
In order to assign the access rights to a user exactly in a system, there is a new role for each area, even though the differences may be slight. This leads to a very large amount of stored information.
The following example illustrates all of this: Consider an organisation with 100 cost centres and 4 organisational roles per cost centre. In the RBAC approach, you need 4 x 100 = 400 groups for this. This number grows as quickly as the number of users and resources that are to be accessed. It is a typical N x M (N users x M resources) problem. Therefore, it is not unusual to have 5-6 times more roles than users.
The limits of LDAP
Another limiting factor of RBAC can be the technology for the implementation. LDAP is mostly used in which the performance to represent groups drops drastically at the moment when the number of users grows beyond 105.
Furthermore, the administrator of the users and the application that interprets the roles both need access to the same LDAP server. That is a massive limitation for a cloud-orientated world in which the organisation of the users is different to that of the service provider.
4 Basic concepts for efficient role and permissions management
With these limitations and the challenges of a new project, we began to design a new approach for role and permission management. To design SecuRole®, we started with 4 basic concepts:
- A role is not represented by the membership in a group, but rather it represents an attribute of a user object. Since the technology can much more easily process user objects than long member lists in a group, there is no longer a limit of 100,000 members per role. This solution can be scaled significantly better.
- A role attribute contains the name of a role, the assignment information and one (or more) optional parameters. The result of this is a fine-grained definition of the access rights and prevents an explosion of roles like in the above example.
- The role attribute is a JSON object. This results in high flexibility. And, we have added additional information such as, for example, the validity date or the approver of a role. A JSON object is a standard and is easy to implement.
- Ultimately, the JSON object is digitally signed and results in a JSON Web Token (JWT). This enables very high security, because the role information is trustworthy. Anyone who trusts the signature also trusts the assignment. In addition, the implementation of a JWT is easy.
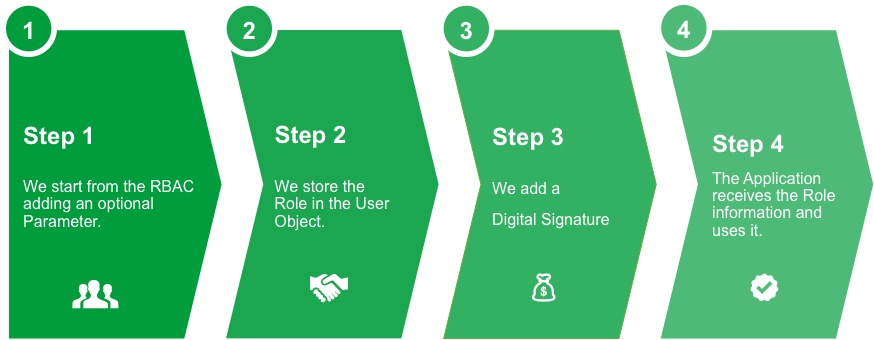
Figure 1: SecuRole® – 4 easy steps to more security
Role assignment
In addition to easy role assignment by an administrator or account manager, Login Master provides the assignment using the ABAC approach (Attribute Based Access Control).
Through this technology, a role is assigned based on specific values of the user or specific attributes of an application. These roles are assigned directly after a user acquires a respective permission. As an example, the membership of a user in a new organisation causes his assignment to the new unit.
A user can also apply for a role via a special application of Login Master: the “Role Shop”. Using the Role Shop reduces the work of support or the account manager even more thanks to different automation mechanisms that run via workflows. With it, simple roles can be assigned automatically. An assignment using the dual control principle lends itself to more sensitive roles.
Your benefits from Login Master and SecuRole®
- You receive a flexible solution to manage roles and access rights. Your applications can use this immediately.
- You have a central place for the assignment of all roles and the access rights. This means less work for your auditing and the required compliance.
- High security and flexibility of your role management through SecuRole®.
- Scalability to millions of users.
- Cloud ready: enables scenarios in which the assignment of a role or alternatively an access right is for an organisation (customer or partner organisation) and the usage is for another company (service provider).




